AWS MFA Setup
Using Yubikey(s) with vegas-credentials in AWS requires you to set up a new Virtual MFA Device in AWS.
The use of Virtual MFA Device is required since we're dealing with OATH Time-based One-Time Passwords (TOTP) MFA for multifactor authentication via CLI – and NOT U2F Device multifactor authentication which can only be used via the Web Console UI.
Go to AWS IAM Users page.
Find your user and choose
Security credentialstab.In the Assigned MFA Device row, choose
Manage: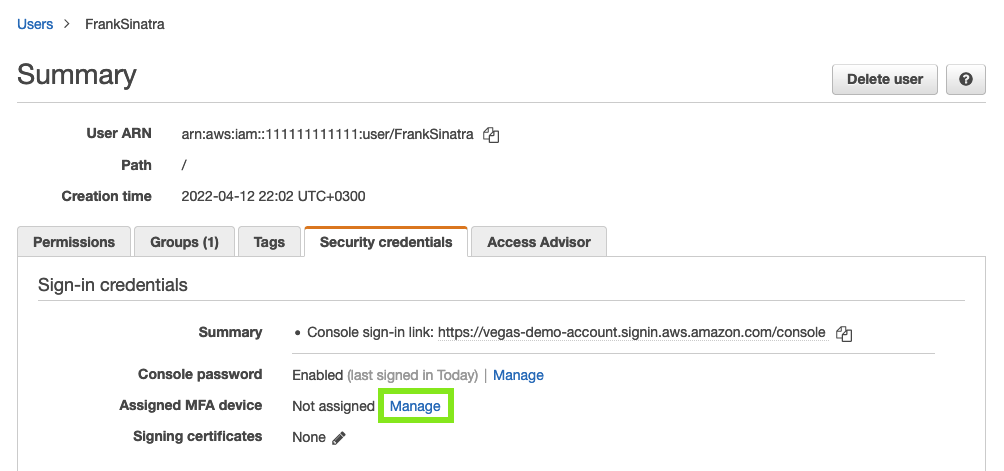
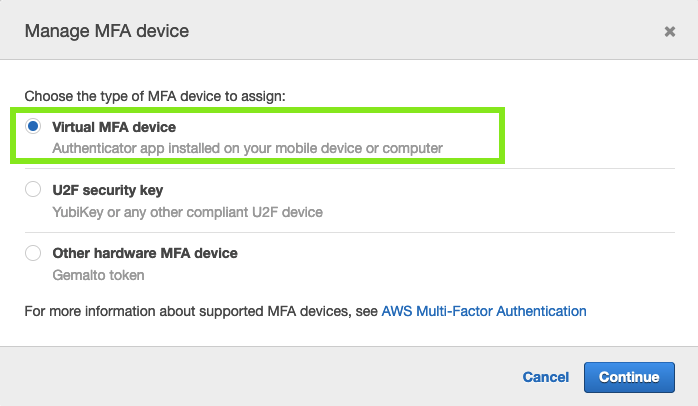
From the new modal dialog choose Virtual MFA Device:
For easiest setup, click Show QR and use Yubico Authenticator GUI to setup:
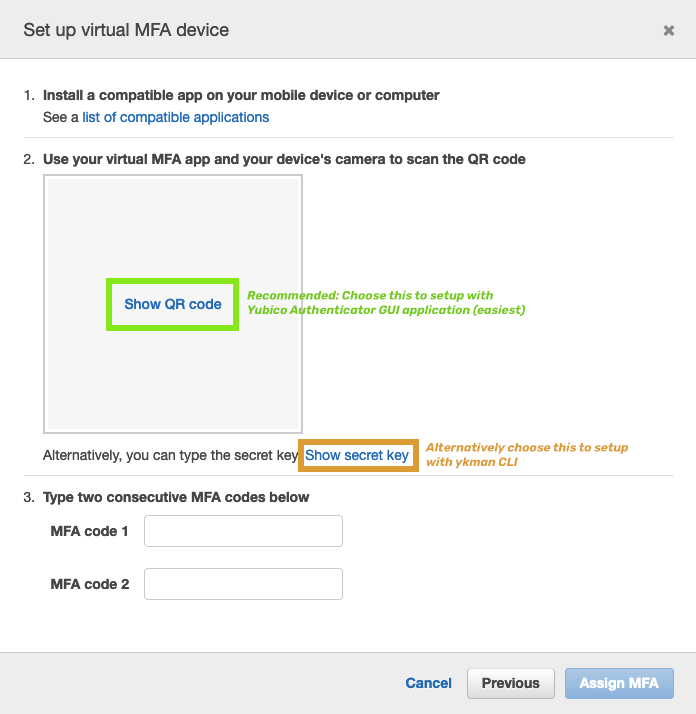
Alternatively you may select Show secret key and use
ykmanCLI to set up the MFA. For reference you may follow these instructions' step 6 and 7.At this point it's useful to scan the QR also into your mobile Authetincator app (such as Authy or Google Authenticator) so they act as a backup. Do NOT use the MFA Codes from the mobile app to configure AWS at this point!
IF you're configuring the MFA here for the AWS Account Root itself, then you definitely should strongly think about MFA backup so that you won't lose access into your account!
- Besides using a mobile Authenticator App as a backup, consider saving the QR code or the secret key into a secure location! For example you could print the QR code and physically save it in a secure location and/or save it into a some kind of secure secrets management system. These are just examples! The root account MFA backup strategy is an important concepts and it is up to you or your organization to define the best & most secure option!
Open Yubico Authenticator and add the new account:
1. 2. 3. 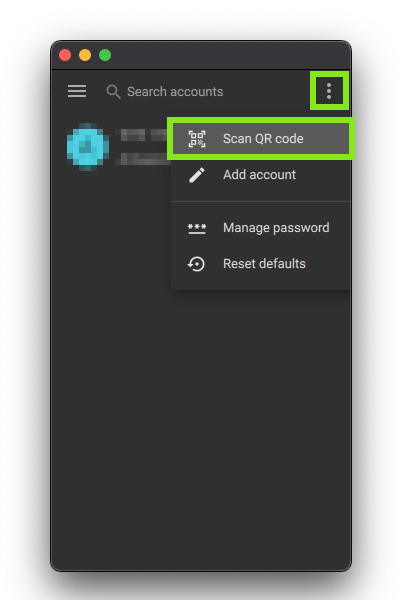
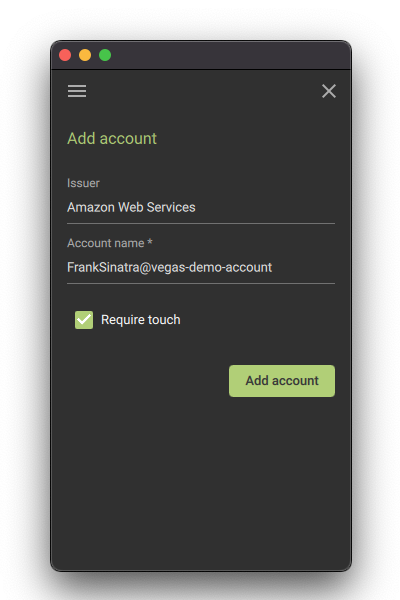
You may also add the account details manually, but the QR scan is the fastest. The QR code in AWS Console UI must be visible to do this.
Once account is added, the issuer should be
Amazon Web Servicesand Account follows the pattern<YourUserName>@<YourAwsAccountAlias>. You MUST leaveRequire touchas enabled!
Paste 2 consecutive distinct MFA codes into the AWS from the Yubico Authenticator:
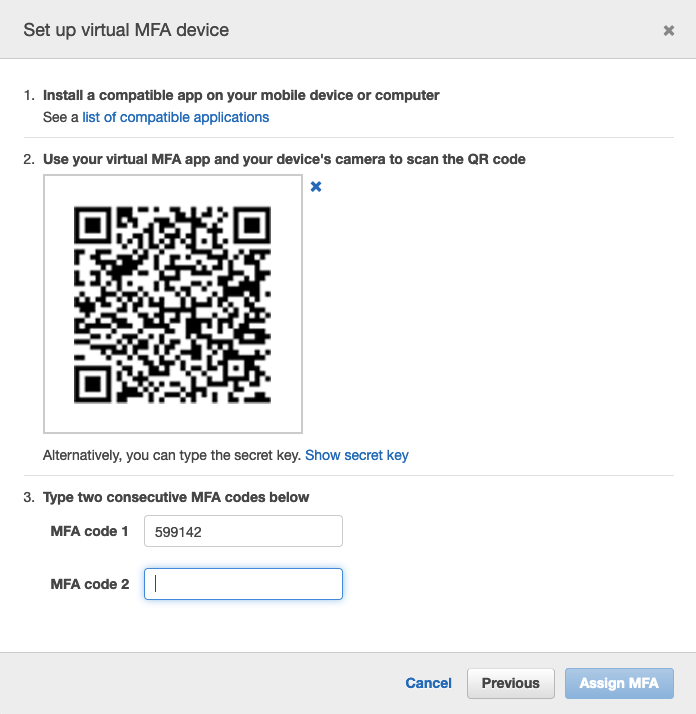
Now the MFA setup in AWS is done:
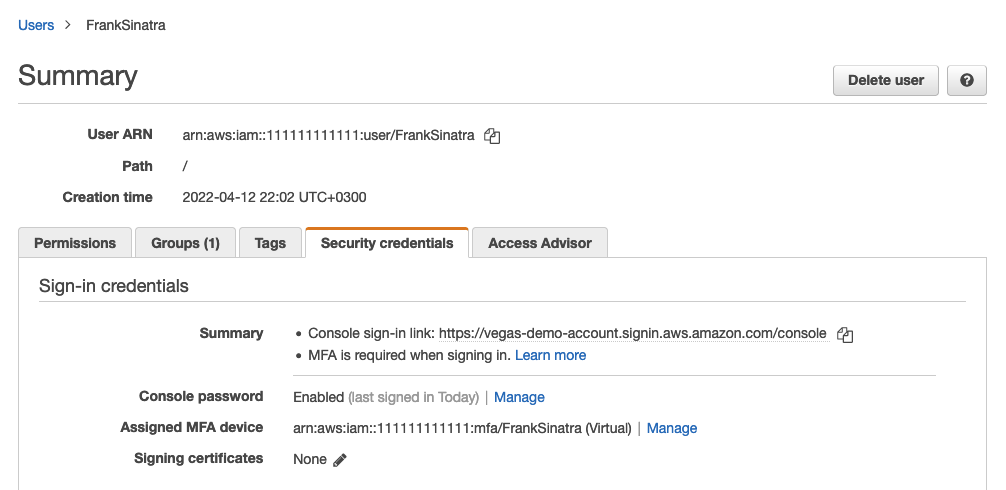
You should sign out and ensure you can sign again into the AWS Web Consule UI with both MFA from the Yubico Authenticator application and from your backup mobile Authenticator App!